It's just a Chinese backdoor like in a lot of Chinese radios.
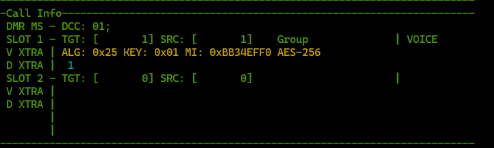
The AES256 DMRA standard defined by Motorola indicates that the encryption is in OFB mode with a 32-bit initialization vector : IV (the famous MI present in the PI Header).
This MI is bound to change with each transmission, this is the case of Motorola, Hytera and even Anytone (but only since a fairly recent update).
At Baofeng the IV (MI) is always the same, it never changes., do the test with an SDR RTL key and capture the images with dsd-fme or DSD+ (test done on a Baofeng DR-1802U) and the whole Baofeng series is probably the same.
You'll see that the MI of the Pi Header is always the same. This is also the case in other Chinese radio stations. You would have thought it was just a bug, but this is very unlikely because every new Chinese radio that offers AES256 always has the same "bug" (backdoor).
If the IV is always the same, you no longer have the security of AES256 at all. For each key you have a flow that always encrypts the same, it is then a simple Vigenere cipher with a key as long as the message.
Since silence frames are repeated regularly in any conversation because you leave silences between words, with about thirty conversations you get the encryption stream (which is always the same in all conversations with the same AES256 key).
You can then decrypt everything without even knowing the AES256 key.
Of course, some people here will tell me: it's not possible, it's AES256 so it's reliable.
Instead of calling me a troll:
1-Check if the MI of the Pi Header is still the same in your Chinese radio
2-If this is the case, ask ChatGPT about the security of such a system (AES 256 in OFB mode with initialization vector always the same) and you will see that it will confirm what I am telling you.
The advantage of this backdoor is that it remains compatible with Motorola or Hytera radios.
Motorola radio or Hytera receives the MI of Chinese radio and decrypts the conversation. Motorola or Hytera firmware does not send any alerts if the MI is still the same because it is not provided for in the DMRA standard.
So you get the impression that it's as reliable as a Motorola or Hytera radio, but that's not the case at all.
In 2020 someone had already found the backdoor at Anytone:
Is there a way to switch between RC4 and AES without going into the CPS and reprogramming the radio?

forums.radioreference.com
Note: Don't ask me to prove what I'm saying with a program or example because it's illegal. Check it out for yourself and ask ChatGPT if you don't believe me.
Take out your rtl sdr key and do the test yourself!