kayn1n32008
ØÆSØ Say it, say 'ENCRYPTION'
Why do you say that?I am very surprised that Cond'e Nast allowed that to be published.
Why do you say that?I am very surprised that Cond'e Nast allowed that to be published.
I just saw this now, sorry for not getting back to you.Why do you say that?


 thehackernews.com
thehackernews.com
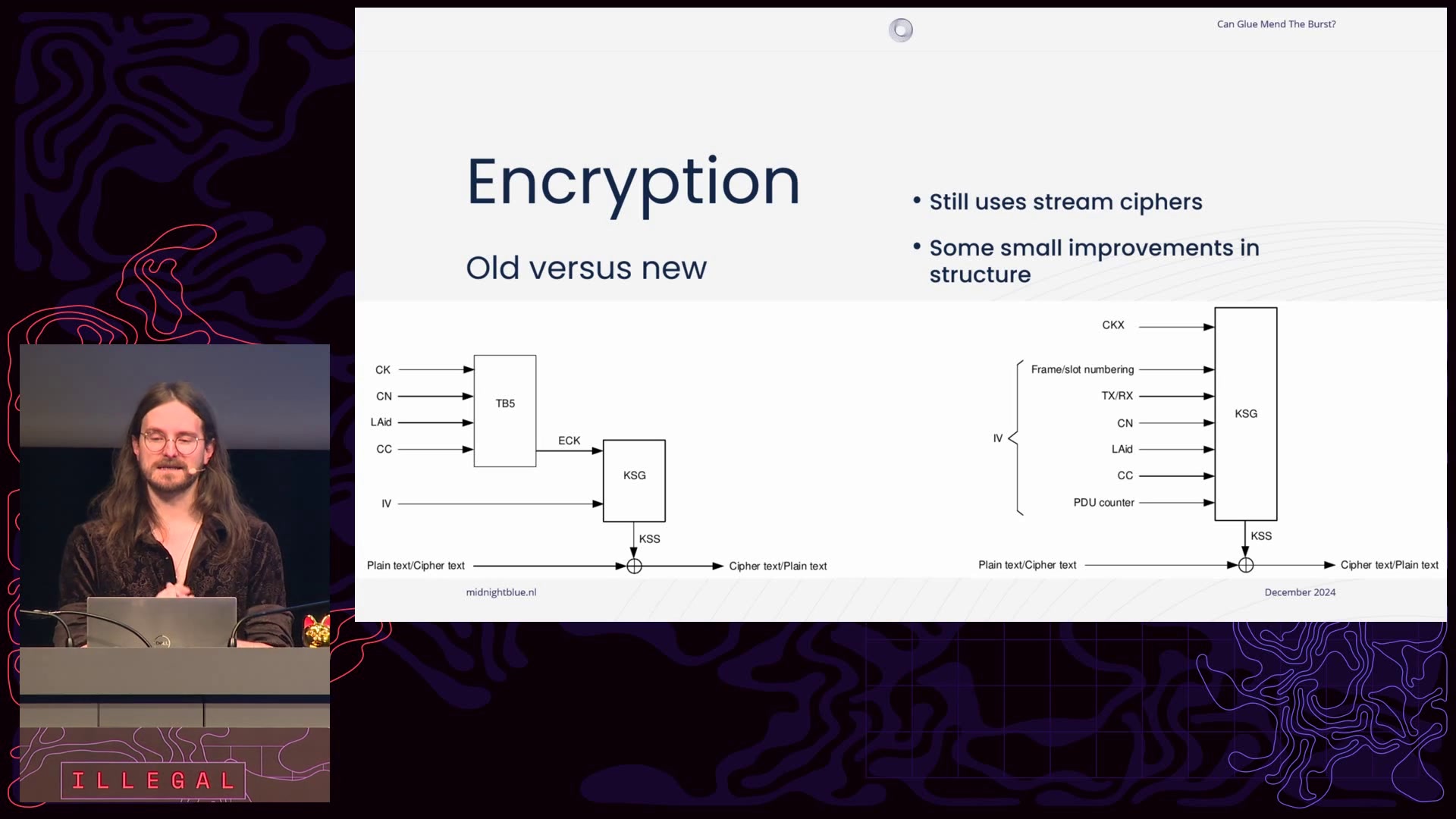
In this talk we will present a practical attack on the TEA7 cipher, which while taking a 192-bit key, only offers 56 bits of security.

No. Currently, there is not enough time OR energy remaining in the entire universe to brute force a PROPER, RANDOM AES256 bit key.
I am obviously talking about a foreign government (Russia, China...) and not a simple citizen.the number of rounds because the 14 rounds of the AES256 (published 25 years ago) are no longer necessarily enough.
Of course the 'Chinese AES256' Radios are less reliable than a FIPS140-2 compliant hardware based radio.
Wassenaar Agreement - Wikipedia
en.wikipedia.org

AES256 encryption and The Wassenaar Arrangement
Hello, I wonder about the Wassenaar Arrangement of which the U.S. is a party, as well as Europe, Australia, India and even Russia. ChatGPT tells me that walkie-talkies are indeed subject to the Wassenaar Arrangement if they use strong cryptography. Part 5b of the Arrangement requires an export...forums.radioreference.com
This suggests that Chinese AES256 radios may be much less reliable than FIPS 140-2 compliant hardware radios that you can only buy with special authorization documents.
I've bought several Astro25 radios, all with AES256, with out any 'special authorization documents'FIPS 140-2 compliant hardware radios that you can only buy with special authorization documents.
Lol, of course current algorithms will eventually be broken. No different than what happened with DES56 ARC4 and other algorithms. Nobody was, is or has suggested that algorithms like AES128/192/256 would remain undefeated forever. Cryptologists are already designing quantum resistant algorithms. It's a dance that will continue on indefinetly, until humans case to exist.Quantum computers will crack the rest of these radio encryption protocols by 2030.
Oh well.
¯\_(ツ)_/¯
I've bought several Astro25 radios, all with AES256, with out any 'special authorization documents'
AES256 isn't an 'American' algorithm, it was designed by 2 Dutch citizens, and was adopted by NIST.
I imported two HF radios from Codan out of Australia. They had AES256.
I had to fill out paperwork and receive approval from the Australian DOD.

AES256 encryption and The Wassenaar Arrangement
Hello, I wonder about the Wassenaar Arrangement of which the U.S. is a party, as well as Europe, Australia, India and even Russia. ChatGPT tells me that walkie-talkies are indeed subject to the Wassenaar Arrangement if they use strong cryptography. Part 5b of the Arrangement requires an export...forums.radioreference.com

