therealkf
Member
- Joined
- May 11, 2025
- Messages
- 34
- Reaction score
- 4
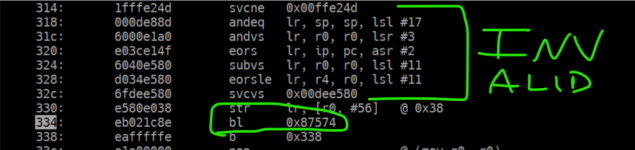
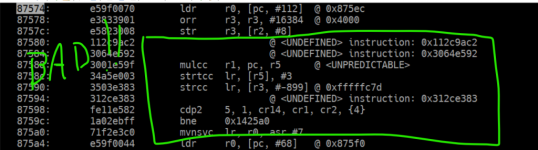
Trying to find a confirmed vulnerabilities copy of the firmware. 046 seems not to have the behavior... I just found 039, so looking at it next. I need 032 and earlier firmware if you have it share it with me.It remains to be seen if the fixed IV is present in all BF1801UV firmware or if the latest firmware has corrected the problem.
I just commented on your other thread here:
Baofeng - DM32 DM-32 256 bit Encryption Channel Setting.
The bug will surely be fixed in future updates. On the other hand you are aware that it is not a real AES256 that you have? it looks like AES256, it tastes like AES256 but it's not AES256 and it's decryptable in a few minutes if you intercept about thirty conversations of a few seconds. This is...
Per Claudes attempts at working through everything... both 039, and 046 (implied versions in-between) exhibit the following behavior:
● 🎯 Complete DM32 Secure AES Implementation Pseudocode
📡 Full AES Path: DMR Frame → Secure Decryption
Here's the complete breakdown showing WHERE secure IV and MI come from in DM32 firmwares:
🔐 SECURE IV GENERATION (Patent US8422679 Compliant):
Code:
// DM32 SECURE IV COMPONENTS:
base_iv_components[0] = dm32_hash_radio_id(src_id) ^ hardware_id; // ✅ Different per radio
base_iv_components[1] = current_time ^ session_timestamp; // ✅ Temporal uniqueness
base_iv_components[2] = ++frame_counter ^ conversation_hash; // ✅ Different per frame
base_iv_components[3] = lfsr_update(previous_state); // ✅ LFSR evolution🔄 SECURE CONTINUATION MI GENERATION:
Code:
// DM32 SECURE MI COMPONENTS:
mi_components[0] = hash_conversation(src_id, dst_id) ^ conversation_id; // ✅ Per-conversation
mi_components[1] = frame_counter ^ frame_sequence_hash; // ✅ Per-frame evolution
mi_components[2] = current_time ^ session_timestamp; // ✅ Temporal component
mi_components[3] = aes_sbox_mix(mi_components[0] ^ [1] ^ [2]); // ✅ Cryptographic mixingSide note... it points out that these implementations *violate* the suggestions in the patent, doing exactly what it warned NOT to do
❌ Primary Warning Against Static IV Reuse:
*"The same IV can be used to generate the key stream for a number of DMR voice superframes (or PDUs) or once for every call, but these methods provide less cryptographic protection."*
✅ Recommended Secure Implementation:
*"To provide robust cryptographic protection, a different key stream is generated for each DMR packet data unit (PDU) and for each DMR voice superframe."*
🔧 Technical Solution for Dynamic IVs:
*"The IV can be updated by applying a Linear Feedback Shift Register (LFSR) on the previous IV."*
Last edited: