I run a Linux RDIO Scanner server through Cloudflared. Love it. And no problem whatsoever with remote SDRTrunk / RDIO servers connecting to my port 443 to feed my RDIO server, and of course no problems with outbound from RDIO. Cloudflared is pretty handy for some things.
You are using an out of date browser. It may not display this or other websites correctly.
You should upgrade or use an alternative browser.
You should upgrade or use an alternative browser.
Cloudflare Origin and ProScan HTTPS server
- Thread starter johndball
- Start date
Very odd indeed. When you added the Origin CA root to Trusted Roots was Powershell Run-As Administrator? I've never seen a valid cert chain fail validation like that unless one of them is expired...It does not work. The ProScan web server does not start as it flags the Origin certificate as an invalid certificate.
@johndball I'm curious, does it still work if you revert ProScan back to the non-custom release version? if so, then Bob @ProScan should be able to revert the change: "I changed the ChainPolicy to AllowUnknownCertificateAuthority"...
That didn't work for me using the old way which was X509Certificate2.Verify without the chainPolicy AllowUnknownCertificateAuthority
Last edited:
ahhhh hold on, I used the ECC CA root in my example fix, maybe try the RSA CA root on your end. Unfortunately I'm unable to fully test on my end as I don't use Origin yet... https://developers.cloudflare.com/ssl/static/origin_ca_rsa_root.pemIt does not work. The ProScan web server does not start as it flags the Origin certificate as an invalid certificate.
Not working for me. Still shows Verify=false. Does this screenshot look okay? and does the computer need rebooting?That look like your importing the actual issued cert into Trusted Roots which won't work since that's making the issued cert appear as a self-signed cert. Remove that from Trusted Roots then try importing both the ECC and RSA certs.
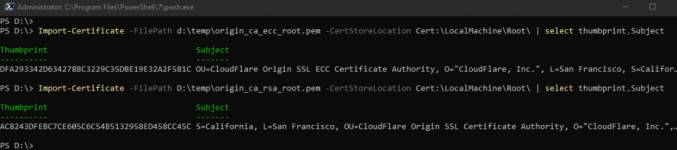
The two Origin root CA certs thumbprints should be:
View attachment 186140
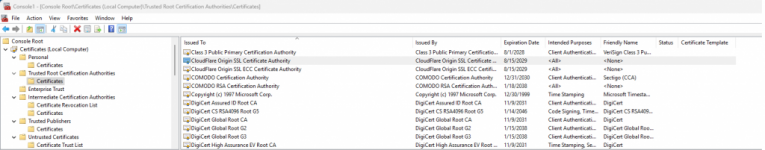
Those two look correct. Take a peek at the Personal\Certificates directory as well as the Intermediate Certification Authorities\Certificates directory to ensure that original cert with "CN=Cloudflare Origin Certificate" didn't end up landing in one of those stores, if it did delete it. Also you might need to re-check those stores in certmgr.msc running just under your user context (not Administrator) as it could have landed there as well. All said, with just those two CA roots in local machine Trusted Roots the "CN=Cloudflare Origin Certificate" *should* verify in Proscan. If not, I'm at a loss to explain this one. Windows certificate management abyss of misery! - edit: maybe also a reboot will flush it out.Not working for me. Still shows Verify=false. Does this screenshot look okay? and does the computer need rebooting?
View attachment 186141
Last edited:
I rebooted the computer then I checked certmgr.msc not running as admin.Those two look correct. Take a peek at the Personal\Certificates directory
I did have one there. I deleted that.
I'm going to reboot the computer again now.
Still not showing cert as valid. Basically this is the code I was using, using .NET Framework 4.8.
Before - Was working great without any issues up until CloudFlare Origin
X509Certificate2 cert = [BouncyCastle routines to get cert and private key]
bool valid = cert.Verify; // returns false using CloudFlare Origin
After
X509Chain chain = new X509Chain();
chain.ChainPolicy.VerificationFlags = X509VerificationFlags.AllowUnknownCertificateAuthority;
bool chainBuild = chain.Build(Cert); // returns true using CloudFlare Origin
Before - Was working great without any issues up until CloudFlare Origin
X509Certificate2 cert = [BouncyCastle routines to get cert and private key]
bool valid = cert.Verify; // returns false using CloudFlare Origin
After
X509Chain chain = new X509Chain();
chain.ChainPolicy.VerificationFlags = X509VerificationFlags.AllowUnknownCertificateAuthority;
bool chainBuild = chain.Build(Cert); // returns true using CloudFlare Origin
Very odd indeed. I haven't used bouncy castle for a good number of years and that was just a small project. There's got to be a reason the API is not seeing those imported Origin CA roots, I just don't know why. I thought bouncy just utilized the Windows built-in cert stores. Can you DM me that ScannerDev_publickey.crt file so I can try to replicate on my end?Still not showing cert as valid. Basically this is the code I was using, using .NET Framework 4.8.
Before - Was working great without any issues up until CloudFlare Origin
X509Certificate2 cert = [BouncyCastle routines to get cert and private key]
bool valid = cert.Verify; // returns false using CloudFlare Origin
After
X509Chain chain = new X509Chain();
chain.ChainPolicy.VerificationFlags = X509VerificationFlags.AllowUnknownCertificateAuthority;
bool chainBuild = chain.Build(Cert); // returns true using CloudFlare Origin
You know your stuff. That's for sure.Very odd indeed. I haven't used bouncy castle for a good number of years and that was just a small project. There's got to be a reason the API is not seeing those imported Origin CA roots, I just don't know why.
Probably can. I'm not using the Windows built-in cert stores at all but rather bouncy to get the cert and key files.I thought bouncy just utilized the Windows built-in cert stores.
To me, the cert stores adds a layer of complications and I rather try to keep it as simple as possible.
I'm not privy to. Perhaps @johndball can.Can you DM me that ScannerDev_publickey.crt file so I can try to replicate on my end?
Last edited:
I can generate any public/private key pair that y'all want to test.You know your stuff. That's for sure.
Probably can. I'm not using the Windows built-in cert stores at all but rather bouncy to get the cert and key files.
To me, the cert stores just adds a layer of complications and I rather try to keep it as simple as possible.
I'm not privy to. Perhaps @johndball can.
If we keep it to DM and the three of us, I will send you the public/private pair I am using on the production server. Give me a few minutes. If you DM me your email, I'll add you to the Cloudflare Access portal so you can pull any data from the stream that may help.
I know enough to get me in trouble! a few years managing Windows ADCA PKI that sometimes I wish I could forget... thank you though. So I noticed that my Letsencrypt cert in the proscan directory is a PFX file which is a self-contained store, it contains BOTH my server cert AND the letsencrypt root CA, it's pretty much a standalone file-based cert store. I'm wondering if creating a new PFX file with these:You know your stuff. That's for sure.
Probably can. I'm not using the Windows built-in cert stores at all but rather bouncy to get the cert and key files.
To me, the cert stores just adds a layer of complications and I rather try to keep it as simple as possible.
I'm not privy to. Perhaps @johndball can.
origin_ca_rsa_root.pem - root CA
ScannerDev_publickey.crt - server cert
would resolve and verify correctly. Unfortunately, if it does work that really doesn't help on your end much unless you were to make bouncy castle use the windows cert store for CA root lookups...
Sorry, this seems to be turning into a personal challenge on my end! and I don't even use Cloudflare Origin LOL.
@ProScan - I rolled the ProScan.exe version back to the original v24 not using the test .exe's that you sent me. I then took the Cloudflare public / private key pair as well as the Cloudflare Origin RSA PEM and combined all three files into a .PFX certificate. I renamed the certificate to letsencrypt.pfx and loaded that into ProScan. The server starts up without issue now.
This may be the route that @ndebaggis was going ...
This may be the route that @ndebaggis was going ...
Attachments
That would be the route I just took as well!@ProScan - I rolled the ProScan.exe version back to the original v24 not using the test .exe's that you sent me. I then took the Cloudflare public / private key pair as well as the Cloudflare Origin RSA PEM and combined all three files into a .PFX certificate. I renamed the certificate to letsencrypt.pfx and loaded that into ProScan. The server starts up without issue now.
This may be the route that @ndebaggis was going ...
So, effectively what we have is, Windows Certificate HELL! I removed all the Cloudflare Origin root CA certs I had installed to test, then only added back the origin root CA RSA file to Windows LocalMachine Trusted Root Certificates, then added @johndball PFX to ProScan. Good to go! Bob @ProScan it looks like you can close this one out! Now maybe I'll actually take a better look the Cloudflare Origin proxy and what it offers.
Thanks for that. I'm have to decide on my end what route to take. 1) Keep it as is (before the test files) or 2) If it is a ClouldFlare Origin cert then use the chain policy AllowUnknownCertificateAuthority. Probably 1.@ProScan - I rolled the ProScan.exe version back to the original v24 not using the test .exe's that you sent me. I then took the Cloudflare public / private key pair as well as the Cloudflare Origin RSA PEM and combined all three files into a .PFX certificate. I renamed the certificate to letsencrypt.pfx and loaded that into ProScan. The server starts up without issue now.
This may be the route that @ndebaggis was going ...
Curious, did you generate the PFX on the Cloudflare admin panel or did you hand-roll it?@ProScan - I rolled the ProScan.exe version back to the original v24 not using the test .exe's that you sent me. I then took the Cloudflare public / private key pair as well as the Cloudflare Origin RSA PEM and combined all three files into a .PFX certificate. I renamed the certificate to letsencrypt.pfx and loaded that into ProScan. The server starts up without issue now.
This may be the route that @ndebaggis was going ...
Did it manually. I too was once an ADCS admin back in the server 2008 IT admin days.Curious, did you generate the PFX on the Cloudflare admin panel or did you hand-roll it?
I would totally go back to the original version 24.0. Allowing unknown CA is pretty big no-no in InfoSec. Sometimes you have no choice but to do it for in-house servers but where your software is out in the wild it's probably not a good option.Thanks for that. I'm have to decide on my end what route to take. 1) Keep it as is (before the test files) or 2) If it is a ClouldFlare Origin cert then use the chain policy AllowUnknownCertificateAuthority. Probably 1.
Similar threads
- Replies
- 25
- Views
- 2K
- Replies
- 6
- Views
- 566